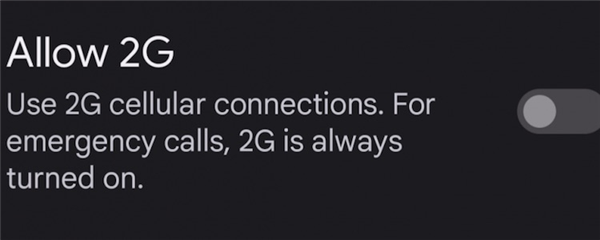
On January 14, Google plans to add an option to switch 2G networks to the new version of Android, allowing users to choose whether to block 2G band signals, which can save most users' mobile phones from being hacked. Now that 4G is blooming almost everywhere, the popularity of 5G is also increasing, and the era of 2G is about to usher in the end.
In some places where the signal of 3G, 4G, and 5G networks is not good, 2G can often exert residual heat, which is why sometimes 2G networks are more active than 3G. However, 2G networks are all 31 years ago, and the technology was born without taking security into account, and the encryption technology is very rudimentary.
2G network in the mobile phone and base station communication between the communication without too much encryption processing, in today's technological means so developed, hackers can easily intercept the user's telecommunications and text messages, and even do not need to send any packets, can hack into the mobile phone. Our mobile phones contain a lot of personal information and private data, and once hacked, the consequences are unimaginable.
On the other hand, the 2G network does not have advanced base station authentication technology, which is also a very popular frequency band for pseudo base stations, and many of the spam text messages and harassment and scam calls we usually receive are sent from these pseudo base stations. Some smartphones are equipped with a pseudo-base station interception function, which is actually one of the means to prevent spam intrusion.
In fact, starting with 4G, the security of the network no longer requires us to worry. However, now that technology is so developed, there are many things that we dare not think about, and some people can do it. Some base station simulators can be downgraded to 2G networks, continue to exploit the above vulnerabilities, even if the network is highly secure and developed today, there are still hackers who can attack mobile phones along the 2G network.
Unfortunately, this feature developed by Google has certain hardware limitations, and is currently only suitable for newer smartphones, and "nail households" who are worried about being attacked can have to consider it carefully, and there is one more reason to change the phone later. In addition, at this stage, the shutdown of 2G functions can only be achieved by Android devices, and the later popularization may also require the help of operators.
In China, in order to make room for 5G, some operators have begun to gradually shut down 2G base stations. However, there are still about 10% of 2G users, and they may still be using button function machines. The complete replacement of 2G base stations is an inevitable result, but operators will not shut down them all in one go. Xiao Lei expects that after the 2G exits the stage, there may be highly skilled hackers eyeing the 3G network, and everyone still has to pay more attention to protecting their own information.